Cyber Risk Mitigation Responsibilities, IU policy IT-28, ensures that the community works to “vigilantly mitigate cybersecurity risks, maximize physical security for IT systems, and minimize unacceptable risks to IT systems and data from natural disasters (collectively, 'Cyber Risks')". This ongoing vigilance is maintained by a cycle of peer reviews of unit risk mitigation strategies/efforts; a two-year cycle is expected. There are two elements that describe the complexity of implementing IT-28, peer review cycles and policy implementation phases.
Peer review
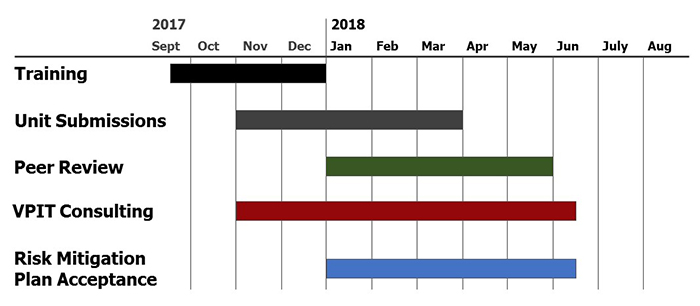
An IT-28 peer review cycle is expected to begin every two years. The first implementation of IT-28 began in May 2013 with the adoption of the policy. The community was given one year to formulate a risk mitigation plan and submit their efforts for peer review by May 2014. Peer reviews for the first cycle of IT-28 implementation were completed in June 2015. Effectively, the first cycle of IT-28 is documented as covering years 2013-2015. Planning for the second cycle (round) of IT-28 began in the third quarter of 2016 and the second peer review cycle is expected to be completed by the second quarter of 2018.
Implementation phases
Each cycle is comprised of seven policy implementation phases: Plan, develop, train, execute, review, accept, and improve. Although phases are not mutually exclusive, they generally describe the flow of IT-28 responsibilities for each cycle. The UISO and UITS are responsible for the plan and develop phases. IU IT Community involvement happens in the plan, execute, review, and accept phases; the execute phase covers the tangible IT-28 responsibilities of risk/security assessment, unit strategy, and appropriate documentation. The improve phase has two audiences -- the IU IT Community who reduces Cyber Risks and the UISO and UITS who strategizes for the next cycle.