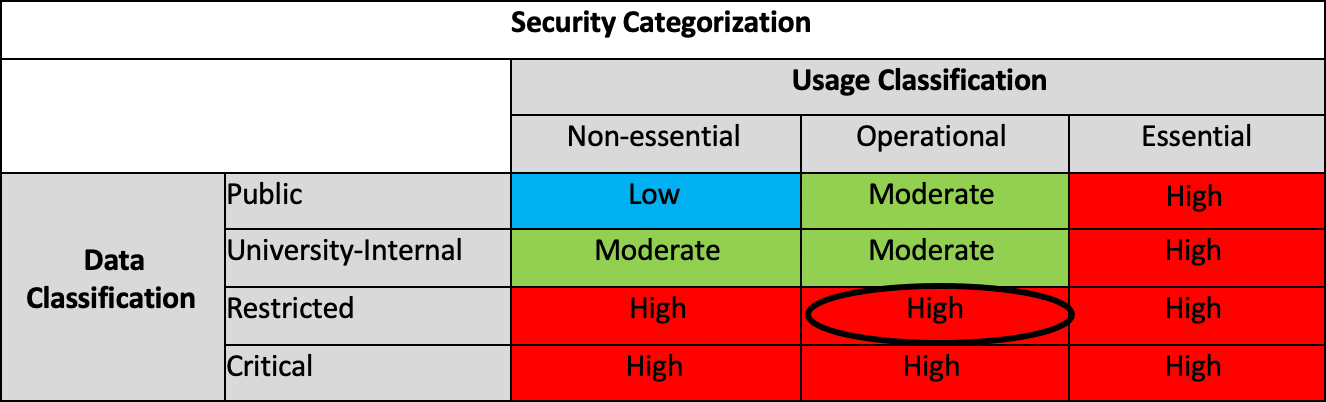
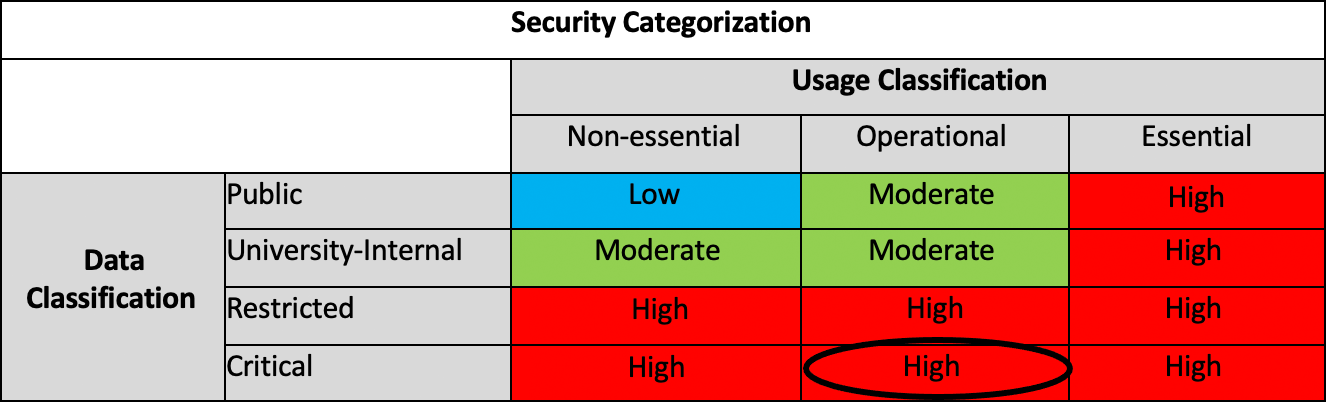
Reason for the Procedure
Information technologies are critical to most if not all Indiana University operations. This dependence has resulted in a large, diverse, and complex technological environment, which in turn has resulted in a greater threat surface and opportunity for intrusion attempts.
As more data is being stored, accessed, and manipulated electronically, the risk to systems increases, as does the risk of unauthorized disclosure or modification of personal, proprietary, or institutional data.
The use of automated scanners and break-in scripts facilitates the scanning of entire networks for vulnerable systems. Systems that are not properly secured will be discovered and can be subject to intrusion and exploitation. Data on vulnerable systems is at risk of compromise, alteration, or destruction. Compromised systems will also be used to compromise or attack other systems.
This procedure supports Policy IT-12 to promote compliance with legal, regulatory, and contractual requirements to safeguard data while protecting university IT resources from compromise.
Definitions
Procedure - Procedures (like standards) support policy by further describing specific implementation details (i.e., the "how"). A procedure can be thought of as an extension of a policy that articulates a process to be used in carrying out/complying with the policy. A procedure may describe a series of steps, or how to use standards and guidelines to achieve the goals of a policy. Procedures, along with standards, promote a consistent approach to following policy. Procedures make policies more practically meaningful and effective. Procedures overlap with standards, although procedures tend to be more focused on process while standards tend to be more focused on requirements or specifications. Because procedures directly support policies, compliance with procedures is nonoptional and failure to follow procedures may result in sanctions imposed by the appropriate university office.
Sanctions
Indiana University will handle reports of misuse and abuse of information and information technology resources in accordance with existing policies and procedures issued by appropriate authorities. Depending on the individual and circumstances involved this could include the Office of Human Resources, Vice Provost or Vice Chancellor of Faculties (or campus equivalent), Dean of Students (or campus equivalent), Office of the General Counsel, and/or appropriate law enforcement agencies. See Policy IT-02:Misuse and Abuse of Information Technology Resources for more details.
Failure to comply with Indiana University information technology policies may result in sanctions relating to the individual's use of information technology resources (such as suspension or termination of access, or removal of online material); the individual's employment (up to and including immediate termination of employment in accordance with applicable university policy); the individual's studies within the university (such as student discipline in accordance with applicable university policy); civil or criminal liability; or any combination of these.
Procedure History
Initial Draft - February 12, 2022
Revised - March 23, 2022 and April 6, 2022
Effective -July 9, 2024